Lean ISMS – Protection of the economic Success of your Company
Lean ISMS provides methods and tools for effective & lean information security based on ISO 27001 and IT-Grundschutz. Through the systematic & lean approach and lean ISMS tool, you will be successful with a bootstrap in just a few months. This can be continuously expanded, certified and extended to other aspects such as data protection or compliance.
Our methods and solutions in information security, data protection & compliance as well as enterprise architecture management and IT service management support you in achieving your goals and leveraging synergies.
We use a holistic, systematic & lean approach to address information security with our methods and tools.
Our Lean ISMS Tool (LeanISMS Starter & Complete) simplifies information security and its management through lean philosophy, pragmatic solutions, directly usable templates and concepts according to our motto “easy & effective” – for companies of all industries and sizes.
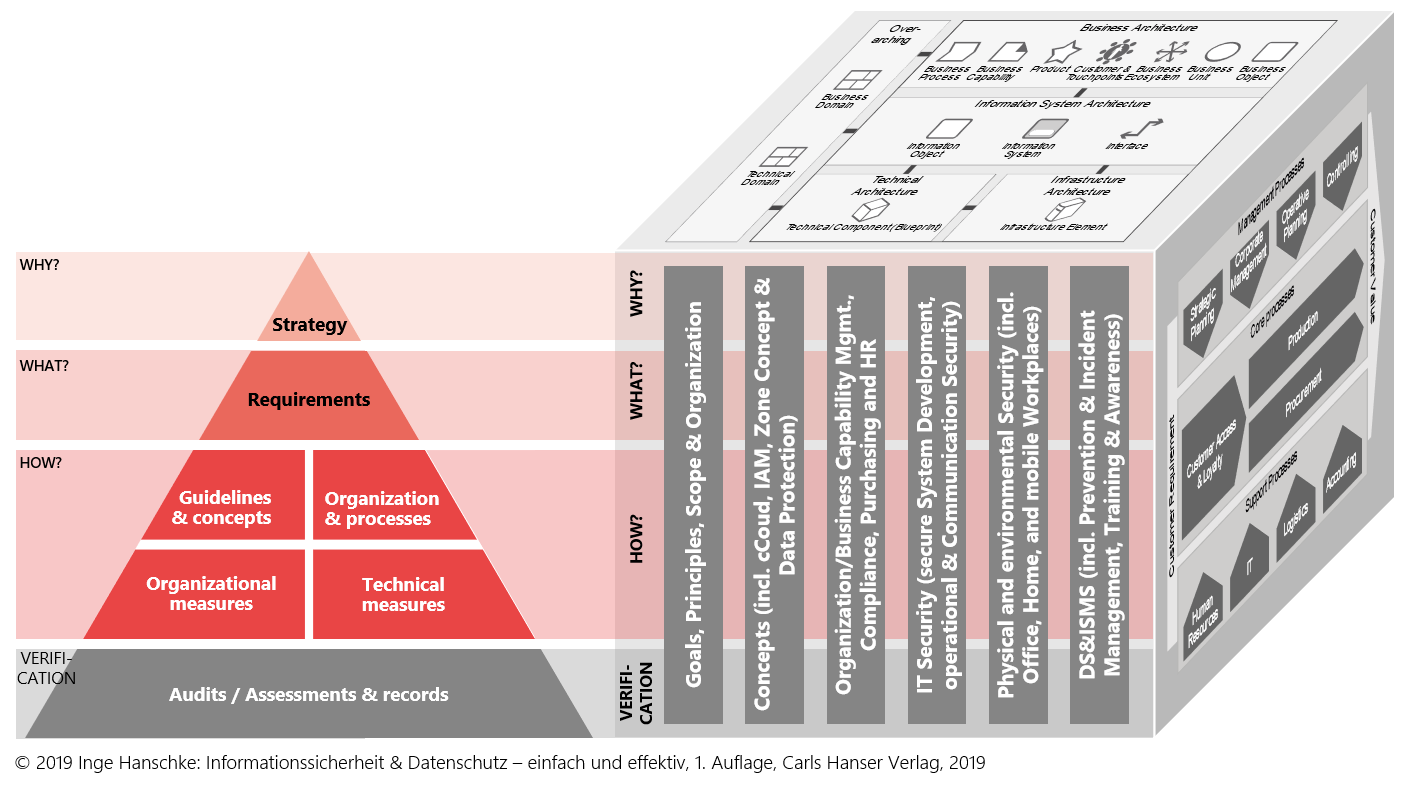
Necessary MUST managed in a lean & effective traceable way
Our Value Proposition
The threat situation and the requirements for information security are continuously increasing. Adequate protection of information and IT systems without restricting the time-to-market development of the business model are critical to the success of any company.
We advise and support you in all aspects of information security and deliver customized solutions for your company.
We support you with the following topics individually or in combination:
ISMS-Requirements/ Use Cases
For a successful ISMS implementation and certification, an Information Security Management System (ISMS) must be established in the organization. The support by a tool must cover all processes and ideally meet the following requirements:
Asset-Management
Inventory of all necessary enterprise assets using e.g. an EAM tool with integration to a CMDB.
Management of Information Security Measures
Management of Information Security Measures (create, change, delete, assign) incl. tracking
Determination of Protection Needs
according to the protection goals, in particular confidentiality, integrity and availability. An EAM tool with integration to a CMDB with survey feature can be used.
Risk Management incl. Risk Assessment &
Risk Treatment
- Variance analysis: e.g. SoA excel with highlighting
- Threat assessment: mapping of the threats to the assets. IT-Grundschutz threat table as a suggestion for selection
- Support in the risk assessment and definition of the risk treatment plan
Management of Security Controls
- Import of Standards and IT-Grundschutz catalogs including their assignment.
- Selection of the requirements relevant for the company. The assignment to the original requirements is retained (crosstabs).
- Editable Statement of Applicability (SoA) and gap analysis template (consistent data in the tool).
Incident & Emergency Management
Link to the IT Service Management System including workflow support with integration into the overall Emergency Management System and reporting functionalities
Prevention
Separate tool for prevention (penetration testing and vulnerability management) and integration with Management of Information Security Measures
and reporting
Internal & external Audits / Assessments
Possibility of entering the audit results and integration into Risk and Measures Management
Awareness and Training
Supporting proof of awareness and training measures
ISMS Monitoring & Reporting
Definition of suitable KPIs and reports.